Node types#
This section contains the node library: reference documentation for every built-in node in n8n.
Node operations: Triggers and Actions#
When you add a node to a workflow, n8n displays a list of available operations. An operation is something a node does, such as getting or sending data.
There are two types of operation:
- Triggers start a workflow in response to specific events or conditions in your services. When you select a Trigger, n8n adds a trigger node to your workflow, with the Trigger operation you chose pre-selected. When you search for a node in n8n, Trigger operations have a bolt icon
 .
. - Actions are operations that represent specific tasks within a workflow, which you can use to manipulate data, perform operations on external systems, and trigger events in other systems as part of your workflows. When you select an Action, n8n adds a node to your workflow, with the Action operation you chose pre-selected.
Core nodes#
Core nodes can be actions or triggers. Whereas most nodes connect to a specific external service, core nodes provide functionality such as logic, scheduling, or generic API calls.
App nodes#
App nodes integrate with specific external services and applications. The specific features differ from service to service, but some common examples include managing resources with CRUD operations, checking and updating statuses, sending and receiving messages, and converting data and documents.
App nodes may be triggers or actions depending on whether they start workflows or not, and many App nodes implement both functions.
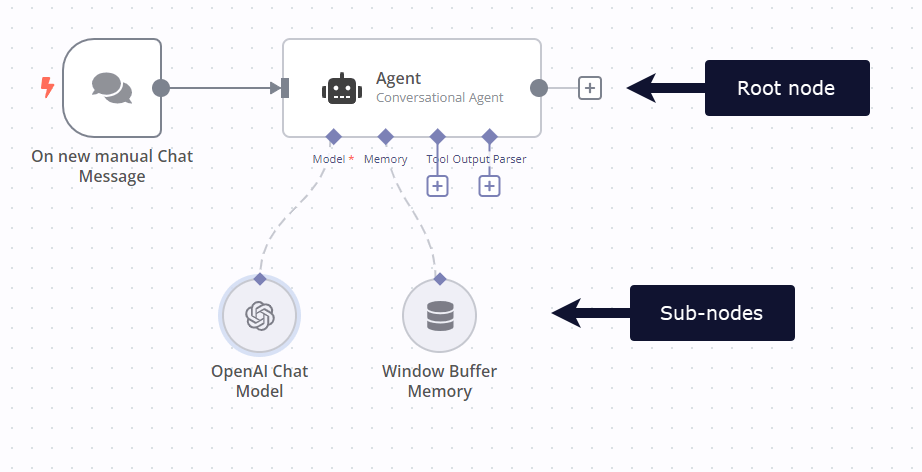
Cluster nodes#
Cluster nodes are node groups that work together to provide functionality in an n8n workflow. Instead of using a single node, you use a root node and one or more sub-nodes that extend the functionality of the node.
Community nodes#
n8n supports custom nodes built by the community. Refer to Community nodes for guidance on installing and using these nodes.
For help building your own custom nodes, and publish them to npm, refer to Creating nodes for more information.
Credentials#
External services need a way to identify and authenticate users. This data can range from an API key over an email/password combination to a long multi-line private key. You can save these in n8n as credentials.
While not nodes themselves, credentials are often required to correctly use nodes. Once saved, nodes in n8n can request that credential information. As another layer of security, only node types with specific access rights can access the credentials.
To make sure that the data is secure, it gets saved to the database encrypted. n8n uses a random personal encryption key, which it automatically generates on the first run of n8n and then saved under ~/.n8n/config.
To learn more about creating, managing, and sharing credentials, refer to Manage credentials.